The solutions we offer in the field of Network and Security, in collaboration with both global and local manufacturers, are detailed below. You can contact us at info@netsys.com.tr for the solutions you need.
![]()
FortiAnalyzer is a network cybersecurity logging and analysis solution developed by Fortinet. It is used to collect logs and generate reports from syslog-compatible devices, including Fortinet products. It comprehensively records network traffic, viruses, attacks, web traffic, application traffic, email, and more, enabling us to prevent misuse of the network and create detailed reports about our network traffic.FortiAnalyzer can be used in large-scale networks to provide critical data for network security and operational performance. It can collect data from various sources, including Fortinet network and cybersecurity devices, user session logs from devices, network traffic data, application usage, and network health status. This data allows security experts to investigate and make sense of events occurring on the network. FortiAnalyzer offers a wide range of reporting options, allowing cybersecurity teams to see what’s happening on the network and adjust their security strategies accordingly.
FortiAnalyzer is an essential part of Fortinet’s Single Pane of Glass security approach. Fortinet offers various security devices to protect your network, and FortiAnalyzer simplifies the interpretation of data from all security layers, including the firewall, IPS, and antivirus protection, by ensuring the integration of these devices.
FortiAnalyzer use cases:
User Behavior Analysis: FortiAnalyzer can monitor and analyze user behavior on the network. This provides network administrators with more information about network users, helping them optimize network performance.
Reporting: FortiAnalyzer collects detailed information about network events and generates reports. These reports assist security teams in better understanding what’s happening on the network and allow them to intervene when necessary.
Performance Monitoring: FortiAnalyzer is also used for monitoring network performance. Network administrators need this information to identify issues in the network and ensure its more efficient operation.
Cybersecurity: FortiAnalyzer enables monitoring and analyzing events in your network. Additionally, it facilitates quick and effective responses when a cyberattack occurs.
Compliance: FortiAnalyzer is a solution for compliance management. Many industries have specific compliance requirements, and FortiAnalyzer can provide the necessary information to meet these requirements.
Efficiency: FortiAnalyzer automates the processes of collecting, storing, and analyzing data in the network. This allows security teams to work more efficiently by spending less time on these tasks.
FortiAP is a series of wireless access points developed and managed by Fortinet. FortiAP devices provide secure and high-performance wireless connectivity for Wi-Fi networks, enabling businesses to manage large-scale wireless networks and minimize cybersecurity risks. FortiAPs can be added to any network to provide Wi-Fi access to employees and guests. FortiAPs come in various models, including 2×2 to 4×4 configurations and models with internal or external antennas, to meet specific requirements.
FortiAP integrates with the Fortinet Security Fabric ecosystem and, when used in conjunction with FortiGate network security devices, provides protection, control, and routing of traffic on the wireless network. The FortiGate device plays a significant role in allowing FortiAPs to be used as a central management and control point.
Key features of FortiAP include:
-
High-Performance Wireless Connectivity: FortiAP supports modern Wi-Fi standards such as 802.11ac Wave 1 and Wave 2, delivering high-speed and reliable wireless connections.
-
Scalability: FortiAP is adaptable to support wireless networks of various scales, from small offices to large enterprise environments.
-
Centralized Management: FortiAPs work in conjunction with FortiGate devices, enabling centralized management of all wireless access points from a single central console. This allows network administrators to easily configure and enforce security policies across their network.
-
Secure Wireless Access: The integration of FortiAP and FortiGate helps monitor, protect, and route wireless network traffic, providing support in blocking malicious software and cyberattacks on the wireless network.
-
Automatic Configuration and Rapid Deployment: FortiAP can be rapidly and easily deployed and configured. Integration with FortiGate devices ensures that new access points are automatically recognized and configured.
-
Indoor and Outdoor Models: FortiAP offers models suitable for both indoor and outdoor use, providing secure wireless connectivity in various environmental conditions.
FortiAP’s scalable and secure wireless access point solutions cater to a wide range of users and address the wireless network needs of businesses and organizations in different industries. It provides solutions for small, medium, and large-scale enterprises, meeting their wireless network requirements securely.
Access and Identity Management
In today’s networks, access and identity management are essential for all roles within organizations. Authentication systems are emerging to ensure security in network and internet access. FortiAuthenticator is an identity authentication and access management solution developed by Fortinet. FortiAuthenticator is used to verify the identities of users and devices, enforce access policies, and control access to network resources. This solution helps businesses and organizations ensure network security, access control, and minimize cybersecurity risks. Additionally, FortiAuthenticator provides a powerful and flexible solution for businesses to establish identity authentication and access control in their networks, increasing security levels accordingly.FortiAuthenticator seamlessly integrates with the Fortinet Security Fabric ecosystem and can be used in conjunction with Fortinet products like FortiGate, FortiAP, FortiSwitch, and more. These integrations enable faster detection of security events and breaches and ensure rapid response times.FortiAuthenticator serves as a user identity management tool, centralizing the storage and management of identity information to create a simple and reliable system.
Key Features of FortiAuthenticator:
-
Support for Authentication Protocols: FortiAuthenticator supports authentication protocols and uses standards such as SAML and OAuth for Single Sign-On (SSO).
-
Two-Factor Authentication (2FA): It offers support for various 2FA methods, including SMS, email, mobile applications, and hardware-based keys, enhancing security by requiring two forms of authentication.
-
Certificate Management: FortiAuthenticator can serve as a Certificate Authority (CA) to issue, renew, and revoke SSL/TLS certificates.
-
Device Identity Authentication and Management: FortiAuthenticator verifies the identities of devices in scenarios such as Bring Your Own Device (BYOD) and controls their access to network resources.
-
Logging and Reporting: It collects and analyzes logs related to user and device access, assisting network administrators in detecting security events and breaches.
-
Centralized Management: FortiAuthenticator provides the capability to manage all identity authentication and access management operations from a single central console.
FortiGate Single Sign On (FSSO):
FSSO is a software tool that enables FortiGate to identify network users, granting access to security policies or VPN connectivity. FSSO allows users to access multiple applications without having to reauthenticate, making it a convenient process.
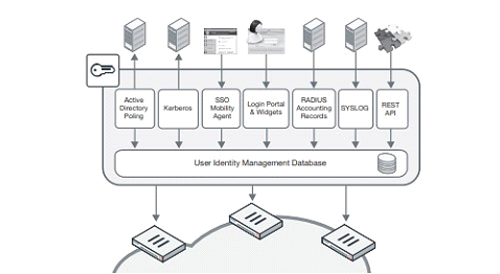
-Enables Identity and Role-Based Security Principles: FSSO activates identity and role-based security principles, securing the corporate network without requiring additional identity verification through Active Directory.
-Simplifies and Centralizes User Identity Management: FSSO simplifies and centralizes user identity management, enhancing corporate security.
-Provides Secure Multi-Factor Authentication with FortiToken: FSSO offers secure multi-factor authentication through FortiToken, enhancing security by requiring multiple forms of authentication.
-Supports Authentication with RADIUS and LDAP: FSSO allows authentication using RADIUS and LDAP, providing flexibility in user authentication methods.
-Offers Certificate Management for Corporate VPN Deployments: FSSO provides certificate management for corporate VPN deployments, ensuring secure access for remote users.
-Supports IEEE 802.1X for Wired and Wireless Network Security: FSSO supports IEEE 802.1X for both wired and wireless network security, allowing for secure access control based on user authentication.
FortiAuthenticator SSO Mobility Agent:
When domain controller queries are not performed or in situations where the domain controller structure is complex, an alternative authentication method used is the FortiAuthenticator SSO Mobility Agent. This agent allows for authentication without the need for domain controller queries in scenarios like login, logout, and changes in IP stacks during wireless network transitions. It can be implemented independently of FortiAuthenticator, either through FortiClient or a client installed on Windows computers. This approach redirects these authentication events to FortiAuthenticator without requiring domain controller queries.
RADIUS Protocol Support:
In a network using wireless or VPN authentication, a user’s RADIUS account information can serve as an identification method. FortiAuthenticator collects packet and group information from a RADIUS server, adds it to FSSO for use with FortiGate devices, eliminating the need for a second authentication. RADIUS packets can be used to trigger an FSSO authentication. FortiAuthenticator also offers integration with FortiToken, certificate management, and more.FortiToken, a two-factor authentication method, is utilized by the FortiAuthenticator series to provide secure remote access. By performing two-factor authentication through FortiToken, users can securely connect to servers. FortiToken Mobile offers options like one-time passwords through SMS and email for authentication.
FortiAuthenticator can be used in various industries to meet identity authentication and access management needs and provide secure network access. Here are some use cases:
-Large Enterprises: FortiAuthenticator provides a central solution for identity authentication and access management on large-scale networks within large companies.
-Telecommunications and Internet Service Providers: Internet and telecom companies can use FortiAuthenticator to provide secure and authorized network access to customers.
-Small and Medium-Sized Businesses (SMBs): FortiAuthenticator assists SMBs in implementing identity authentication and access control on their networks while reducing cybersecurity risks.
-Financial Institutions: Banks and financial service providers use FortiAuthenticator to secure network access, protecting sensitive customer information and transactions.
-Industrial and Manufacturing Facilities: Factories, warehouses, and industrial facilities may prefer FortiAuthenticator for ensuring secure network access and device management.
-Healthcare Sector: Hospitals, clinics, and other healthcare organizations can use FortiAuthenticator to provide secure network access for medical devices and all employees.
-Retail and Service Industry: Businesses in the retail and service sectors, such as stores, restaurants, and hotels, can utilize FortiAuthenticator to offer secure network access to customers and employees.
-Public and Government Organizations: Local governments and government agencies can choose FortiAuthenticator to provide secure network access for employees and citizens.
What is FortiDeceptor ?
FortiDeceptor is designed for deception and represents the next-generation of honeypot solutions. It is capable of detecting and eliminating advanced attacks, including revealing ongoing attacks. FortiDeceptor automates the deployment of traps, identifies attackers, and prevents them from causing damage. It can integrate with Fortinet Security Fabric and FortiGate Firewalls, providing end-to-end protection. By incorporating FortiDeceptor into your breach protection strategy, you can expand your defense perimeter. Security alerts can be configured for detected breaches using unauthorized entry-based detection, allowing for responses to these security alerts. FortiDeceptor can deploy multiple traps and bait to help hide critical systems behind a deceptive layer and protect them from attackers.
Advanced Threat Deception
Deceive
With FortiDeceptor, you can create deceptive internal and external traps and deploy traps and bait through Vm tokens from a central environment. It can deploy Windows, Linux devices and even create SCADA systems that are indistinguishable from real systems, luring attackers into revealing themselves.
Expose
Early and accurate detection systems enable you to receive alerts related to hacker activity and take action. Attackers can be tracked, their activities can be correlated, enabling detailed forensic analysis and gaining insights into the lateral movement of hackers.
Eliminate
It isolates attackers and, by integrating with FortiGate, can cut their connections. This effectively stops attacks and prevents the spread of malware within the network.
Key Features
Wizard-Based Deployment of Trap Vm Tokens: Both enterprise and SCADA networks can be created using Vm through a wizard.
Monitoring and Correlation of Events: Information regarding entry/exit into trap Vms, lateral movement, file uploads, changes, deletions, and execution can be viewed and correlated.
Mitigating External and Internal Attacks: It identifies attackers and lures them into traps, preventing the spread of malicious software within the network.
Security Fabric Integration: It identifies the source of an attack and isolates it with FortiGate integration. Together with FortiSIEM, it offers comprehensive event management and visibility.
Creation of Custom and Comprehensive Reports: Comprehensive PDF reports can be generated via the GUI interface.
Configuration of Alerts and Alert Notifications: FortiDeceptor supports sending email, SNMP traps, and syslog data with notification configuration.
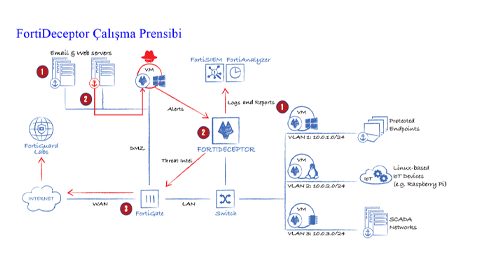
FortiDeceptor sends attacks on real IT and OT assets to traps and bait Vms, and it is indistinguishable from real devices.
When FortiDeceptor detects an attacker, the alert system is triggered. Depending on the configuration, it sends alerts and, if integrated with SIEM, sends SIEM logs. Additionally, FortiDeceptor analyzes its actions through security filters and associates them with a timeline. This provides a centralized view of an attacker’s threat planning.
FortiDeceptor allows security analysts to manually remediate, investigate, or automatically block these attacks. Through integration with FortiGate, it can quarantine an IP address and take measures to prevent major damage from occurring.
FortiEDR Solution: What Is It?
FortiEDR is a cloud-based advanced artificial intelligence endpoint protection, threat detection, and response system. It offers coordinated incident response in real-time for devices with both current and older operating systems, including workstations, servers, communication devices, and industrial and operational technologies. FortiEDR provides effective protection with automated flexible deployment options and predictable operational costs.FortiEDR (Endpoint Detection and Response) is not a standalone product but rather a part of Fortinet’s cloud-based security platform, FortiEDR. It is offered by Fortinet as its proprietary solution and includes features such as malware detection, behavior analysis, threat hunting, and incident response. FortiEDR employs various technologies to detect and prevent various malicious behaviors.
Key Features:
FortiEDR helps reduce attack surfaces, including proactive risk reduction policies, by providing security vulnerability assessments and communication controls for applications and applications with known security vulnerabilities.
It utilizes a next-generation machine learning-based antivirus (NGAV) engine that uses core-level technology developed by Fortinet to prevent the spread of file-based malicious software.
FortiEDR is highly effective in real-time detection and prevention of advanced attacks, even without compromising endpoint security.
It eliminates wait times and provides detection and response capabilities in its methodology for detecting, mitigating, investigating, responding, and remediating incidents (Endpoint Detection and Response).
FortiEDR detects and prevents advanced threats and real-time breaches, even on compromised devices, ensuring data protection and system continuity.
How FortiEDR Works:
FortiEDR provides advanced real-time protection for endpoints before and after the malware infection. It proactively reduces attack surfaces, prevents malware execution, and offers real-time threat detection and response with customizable playbooks. FortiEDR enables automatic incident detection and response without overwhelming security teams or interrupting business operations.
Threat Analysis:
FortiEDR uses behavior-based threat detection technologies to detect and analyze threats. When malicious behavior is detected, FortiEDR analyzes what the threat is and how it behaves.
Alert and Reporting:
FortiEDR generates alerts and reports as soon as malicious behavior is detected, providing details of the incident. These alerts are sent to the security team or responsible individuals.
Response and Remediation:
FortiEDR offers automatic or manual responses to prevent and rectify malicious behavior. Responses may include actions like terminating applications, isolating malicious files, or updating systems based on the type of attack. It automates and streamlines the incident response process.
To improve and remediate, consider these steps:
- Identify the source of malicious behavior and assess all systems.
- Create an appropriate response plan based on the type of attack or infection.
- Apply updates, close security vulnerabilities, and keep security software up to date.
- Regularly scan systems and remove malicious software.
- Develop suitable security policies for your organization and train employees. FortiEDR provides features that support these steps.
FortiEDR Benefits:
Protection: FortiEDR provides proactive, real-time, and automated endpoint protection through coordinated responses to events across platforms. It prevents threats and data breaches, even in compromised devices.
Management: It offers a unified console with an intuitive interface, automating common endpoint security tasks to reduce the time employees need to spend on them.
Scalability: FortiEDR can be quickly deployed and scaled to protect hundreds of thousands of endpoints.
Flexibility: It covers various enterprise use cases and can be deployed within the corporate environment or in a secure cloud. Endpoints are protected both online and offline.
Cost: FortiEDR’s low and predictable costs minimize post-breach operational expenses and harm to the organization.
FortiEDR Features:
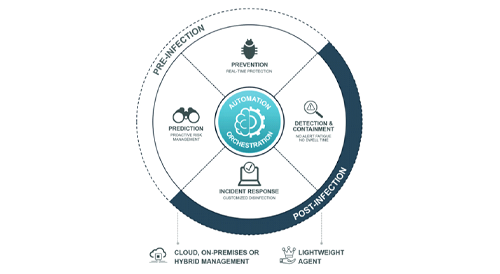
Discover and Predict:
Identify and control vulnerable or unmanaged devices, including malicious devices and IoT devices.
Monitor applications and ratings.
Reduce attack surfaces with risk-based proactive policies, ensuring business continuity even on compromised devices.
Prevent:
FortiEDR uses a machine learning-based virus protection engine to stop the execution of malware. It can be configured with cross-platform NGAV features.
It uses a real-time threat intelligence system from a continually updated cloud database to perform queries and take actions.
Protect disconnected endpoints with offline protection.
Monitor and intervene when USB devices are controlled and malicious activity is detected.
Detect and Defuse:
FortiEDR detects and defuses data leaks, fileless malware, and other advanced attacks in real-time to protect data.
It prevents data leakage, command and control (C&C) communications, unauthorized access to files, and ransomware encryption.
It also continues to collect additional evidence in the background and applies automated incident response playbook policies.
Investigate and Hunt:
FortiEDR enriches data automatically with detailed information on pre- and post-malware events to conduct digital forensics on compromised endpoints.
It automates investigation with minimal interruption to end users.
Automatically defuse and block threats.
Provides protection even when a device is offline.
Protects against memory-based attacks and preserves memory snapshots for fileless threat hunting.
Offers an intuitive interface with clear explanations when an event is marked as suspicious or malicious.
Respond and Remediate:
Conduct incident response operations using inter-environmental communication and custom playbook actions, facilitating incident response and remediation processes.
Automate incident classification and increase alert rates.
Standardize incident log procedures through playbook automation.
Automate incident response actions, such as file removal, process termination, reversing persistent changes, notifying users, isolating applications and devices, and creating tickets.
Automate the removal of threats, recovery of systems, and reversing malicious changes while preserving system uptime.
FortiEDR Security Fabric Integrations:
FortiEDR leverages the Fortinet Security Fabric architecture and integrates with various Fortinet products, including FortiGate, FortiNAC, FortiSandbox, and FortiSiem.
FortiGate: FortiEDR shares endpoint threat intelligence and application information with FortiGate.
FortiEDR management can take actions, such as isolating an IP address, after a breach.
FortiSandbox: Integrates with FortiSandbox, which conducts real-time analysis and classification of files by sending them to a cloud-based virtual environment. It also shares threat intelligence with FortiSandbox.
FortiSiem: FortiEDR sends events and alerts to FortiSiem for threat analysis and forensic investigations. FortiSiem includes a pre-built parser for FortiEDR and can further integrate with FortiEDR using JSON and REST APIs.
FortiNAC: FortiEDR shares endpoint threat intelligence with FortiNAC and supports management through syslog sharing. It can provide instructions for advanced issues like device isolation.
FortiGate solutions encompass all the following cybersecurity functionalities, catering to a wide range of environments, from small offices to Telco operators:
Firewall, VPN, and Traffic Shaping
Intrusion Prevention System (IPS)
Antivirus/Antispyware/Antimalware
Integrated Wireless Controller
Application Control
Data Loss Prevention (DLP)
Vulnerability Management
IPv6 Support
Web Filtering
Antispam
VoIP Support
Layer 2/3 Routing
WAN Optimization & Web Caching
Features of FortiGate Firewall:
FortiGate offers high-performance threat protection functions, such as web filtering, antivirus, and application control, ensuring that your business remains safe from cybersecurity threats like malware infections.
Security Ratings:
It adheres to “best practice” security measures with security ratings provided by FortiGate.
Security Fabric Integration:
It shares threats across the entire IT security infrastructure to provide rapid and automated protection.
Independently Verified and Continuous Threat Intelligence:
It safeguards you against known and unknown attacks.
Mission-Critical Application Protection:
It offers highly scalable segmentation and ultra-low latency for protecting network segments.
Automated Risk Assessments:
It alleviates the burden on IT departments through automated workflow and audit features.
Enterprise-Class Security Management:
It enables remote management of security assets, regardless of location.
What is Forti Isolator?
In today’s digital landscape, advanced threats are on the rise, making it nearly impossible to stay current on which web pages harbor threats and which objects have malicious intent. Keeping up with the proliferation of advanced attacks can be daunting.Fortinet’s browser isolation platform, Forti Isolator, adds an advanced threat protection feature to the Fortinet Security Fabric, ensuring the protection of critical business data from complex web threats. Additionally, it provides access to web content and files in a remote container and then delivers safe content to users.Forti Isolator allows organizations to keep their most critical, high-value assets safe from threat attacks and enables users to browse the web in an isolated environment that generates secure content without the need for installation on the user’s computer or device.
Benefits of Forti Isolator:
- Secure Internet Content Access: User activity on the web is protected from potentially risky web content by passing through a remote isolation environment.
- Clientless Browser Access: Content is processed through any modern HTML 5 browser, eliminating dependencies on specific devices or applications.
- Security Fabric Integration: Forti Isolator seamlessly integrates with FortiGate, FortiMail, and FortiProxy to add an extra defense layer against advanced web-based threats.
- Increased Productivity: Clientless browser isolation keeps employees on the move and focused by rapidly delivering secure web content.
- Effective Use of Data Security: This added layer of advanced protection enhances security for your high-value data.
- Efficient Resource Utilization: It helps reduce memory leak issues, prevent computer slowdowns, and focus valuable personnel resources on proactive support.
FortiMail – Email Security Gateway
Today, email is one of the most effective means of communication. However, it also leads to the spread of viruses, worms, spyware, and spam emails. FortiMail is an advanced email security solution within the Fortinet product family, designed to provide email security, prevent data loss, facilitate compliance with legal regulations, and offer flexible deployment options. FortiMail is a customized email security system that provides multi-layered protection against various threats, including unwanted emails, viruses, worms, and spyware.
FortiMail features a custom operating system that cleans emails through security gateway systems, using antispam, antivirus, and antispyware engines. To ensure up-to-date email protection, FortiMail systems utilize Fortinet FortiGuard antivirus, antispyware, and antispam update services that are updated 24/7 worldwide. It also offers high service quality, virtualization, and archiving features. Additionally, FortiMail is a product with robust routing capabilities.
FortiMail Product Features:
- Multi-Layer Spam Protection: Nowadays, spam emails not only cause a loss of productivity but can also lead to financial and reputation losses through phishing attacks aimed at your organization’s accounting, purchasing, or management units. Additionally, sending bulk emails from your organization’s domain can get it blacklisted. FortiMail checks the SPF, DMARC, and DKIM rules of sending addresses after performing IP address and domain checks on spam emails. It then examines the structure of the message, its digital signature, specified content, image files with image analysis, and the included links through behavioral analysis, providing high protection (up to 99.98%) against spam emails.
- Advanced Antivirus Protection: Viruses transmitted through email can cause data loss and financial losses for individuals and organizations. Since email accounts are accessed from different devices and platforms (web page, computer, smartphone applications, etc.), endpoint antivirus protections fall short in ensuring email security. FortiMail is positioned in front of the email server, preventing unwanted emails from reaching your server. It can clean known viruses and can also integrate with FortiSandbox to clean unknown or polymorphic viruses and stop zero-day attacks.
- Data Loss Prevention (DLP): Like other DLP products, FortiMail offers word and dictionary-based protection and, additionally, takes the fingerprint of files to prevent sensitive data loss by preventing file format changes.
- Identity-Based Encryption (IBE): Important emails you send can be forwarded to other recipients without your consent. If you only want the recipient to read the email, the email must be encrypted, and the encryption key must be sent to the recipient. FortiMail can automatically apply email encryption to selected users or domains. It encrypts the email before it reaches the recipient, who can access the email through FortiMail’s web interface after verifying their identity. Alternatively, FortiMail can convert your email into a web page format and send it to the recipient encrypted. The recipient can access the email in a web page format on their computer after verifying their identity through FortiMail’s web interface.
- Multi-Platform Support: FortiMail can be deployed as a physical device, virtual machine, AWS and Microsoft Azure service, Office365, and Google G-Suite service. Its user-friendly interface simplifies the configuration of your organization’s email security settings.
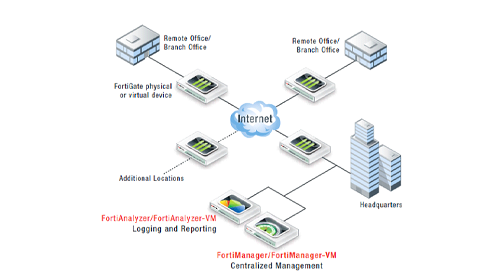
FortiManager – Centralized Management Platform for FortiGate Devices
The FortiManager Centralized Management Platform provides the necessary tools for the efficient management of all Fortinet security systems. FortiManager enables the centralized management and workflow control of Fortinet products from a single console, particularly designed for medium and large-scale infrastructures.
The tools offered by FortiManager streamline tasks such as managing from a few to thousands of devices related to FortiGate systems and FortiClient software. It simplifies the distribution of updates and the enforcement of security rules on managed systems. FortiManager systems feature capabilities like automatic recognition of new devices to be managed, group management, audit mechanisms, and VPN connection management.
When the FortiManager platform is complemented with FortiAnalyzer centralized logging and reporting tools, it becomes a comprehensive and robust centralized management solution.
The FortiManager central management system takes care of the installation, monitoring, and maintenance of Fortinet security solutions. Its secure web-based user interface serves as a starting point for all major management functions. The Device Manager and FortiClient Manager modules are used in conjunction with FortiGate and FortiClient systems from the installation phase to maintenance. FortiManager provides powerful tools that facilitate the management of the managed systems. With local caching of updates and databases using FDN services, it ensures low response times for web filtering and antispam queries. It reduces the time required to apply antivirus and IPS updates.
FortiManager also offers significant functions in terms of monitoring, analysis, and reporting. The Real-Time Monitor module of FortiManager provides easy access to the necessary information for monitoring complex networks. When combined with FortiAnalyzer, FortiManager systems can deliver advanced real-time historical reporting, logging, and data mining capabilities.
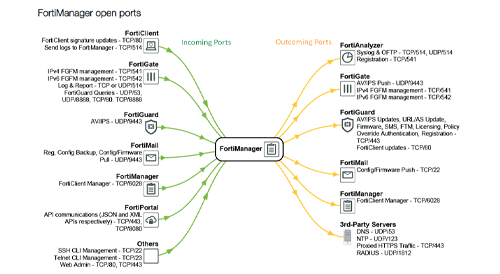
Communication and Integration of FortiManager
FortiManager communicates with devices using several protocols. Each of them communicates over different protocols for Device Manager, FortiGuard Manager, and FortiAnalyzer features.
In general, the ports that are open through FortiManager can be seen in both incoming and outgoing directions.
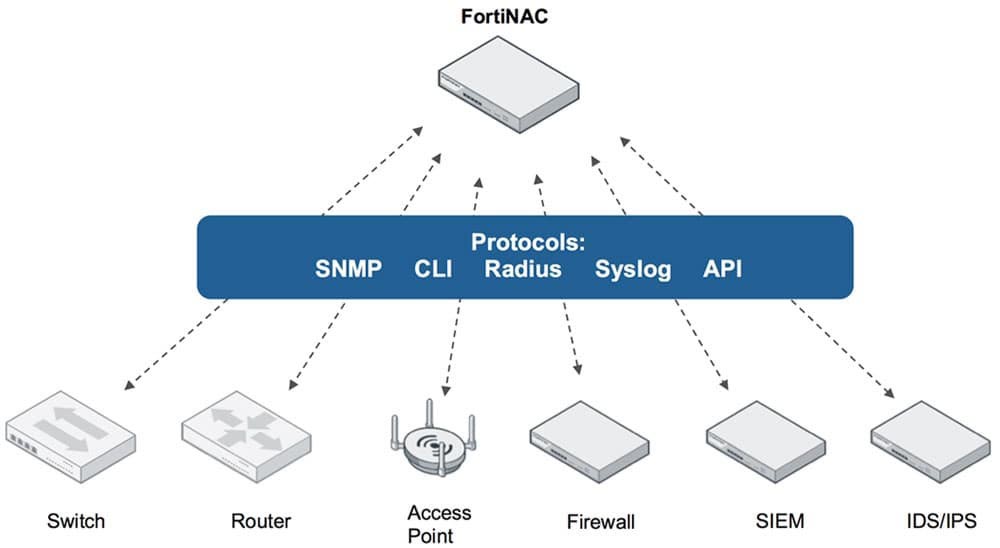
What is FortiNAC?
NAC (Network Access Control) is a solution that controls access to a network. FortiNAC is an effective network access control solution developed for the Fortinet Security Fabric. While providing protection against IoT threats, FortiNAC also offers control over third-party devices and automatically responds to various network events. While the primary function of NAC mechanisms is network access control, it differs from other network authentication and authorization servers. Traditional network authentication implements the IEEE 802.1x standard, which provides an authentication method for devices that want to join the local area network (LAN) or wireless LAN. FortiNAC, on the other hand, is a port-based network access control mechanism that controls access to the network through agent software running within client devices. Another method is to connect to the network via a Captive Portal, for example, in public areas like airports, where access is granted after providing identity information and accepting legal conditions on a web portal.
Agents installed on the computers of clients on the network examine the conditions on networked computers by controlling antivirus updates, operating system updates, and user authentication via Active Directory. However, with the emergence of portable wireless devices, businesses have started allowing the inclusion of BYOD (Bring Your Own Device) and BYOD devices for their benefits in terms of business continuity. Yet, this practice brought some network risks along with its advantages. In parallel with these developments, Internet of Things (IoT) devices have also started to be integrated into network systems. IoT devices that can collect and be controlled lack identity authentication systems and do not support security software, causing security vulnerabilities in the network.
To ensure there are no network risks, BYOD and IoT devices must be controlled, monitored, and managed. FortiNAC profiles such IoT and BYOD devices for network access control, ensuring that they only have access to necessary resources. The FortiNAC solution features a centralized architecture for effective control of large and complex network infrastructures.
Key Features of FortiNAC
Agentless network scanning for device detection and classification.
Creating an inventory of all devices on the network.
Event reporting to SIEM with detailed contextual data to reduce incident investigation time.
Evaluating every endpoint’s risk on the network.
Automating quarantine for your users and guests.
Applying dynamic network access control and enabling network segmentation.
Multiple built-in reports for network reporting, compliance, and analysis.
What is the advantages of FortiNAC?
Network Detection for Every Device and User
The security foundation of a constantly changing network lies in understanding its structure. The FortiNAC solution scans your network using agentless methods to discover every user, application, and device. FortiNAC can scan with up to 13 different techniques, then profile each element based on observed characteristics and behaviors. Additionally, it can notify the need for software updates to address security vulnerabilities. Suitable role-based network access policies can be applied within FortiNAC to protect critical data and sensitive assets, ensuring compliance with industry and government regulations.
Integration with Third-Party Products for Network Control and Easy Setup FortiNAC can apply segmentation policies and modify configurations on switching and wireless products from over 70 manufacturers. Once devices and users are identified, FortiNAC ensures that devices and users are prevented from accessing irrelevant resources, providing detailed network segmentation.
FortiNAC uses dynamic role-based network access control by grouping applications to logically create network segments and limit access to specific user groups. This limits the ability of a device to move around the network and attack other resources if it is compromised.
Ensuring the integrity of devices before they connect to the network minimizes the risk of malware spreading. FortiNAC verifies a device’s configuration when it attempts to join the network and, if an incompatible configuration is detected, it can isolate the device or move it to a limited-access VLAN. Additionally, FortiNAC continuously monitors the network and adjusts access levels based on changes in behavior.
FortiNAC can respond to threat content within seconds before events spread throughout your network. It offers a wide and customizable set of automation principles to trigger configuration changes when observed behaviors indicate a threat.
FortiNAC is a flexible and scalable solution suitable for a wide range of deployments, from medium-sized businesses to large enterprise distributions. It can be deployed on virtualization platforms such as Hyper-V and Vmware or on physical servers.
FortiSandbox Solution
In today’s world, sandbox solutions are used to detect advanced and targeted attacks, prevent zero-day attacks, analyze the behavior of suspicious applications, and detect and clean new malware. Applications are run in sandbox systems, which can be a virtual environment, and their behavior is analyzed to determine whether they are malicious or not.
Fortinet’s FortiSandbox, one of the products with the highest score in the industry benchmark, is among the best solutions to rapidly address evolving and increasingly targeted threats across a wide digital attack surface that pose unknown malicious threats to your systems.
The advantage offered by FortiSandbox as a next-generation security mechanism is its ability to provide security as a system that can analyze, understand, and take action on threats that traditional security systems have failed to detect. It is an effective solution for detecting advanced attacks that are difficult to detect, can bypass traditional intrusion prevention systems, and exploit zero-day vulnerabilities. The sandbox is designed with strict control and permission mechanisms, providing a separate and restricted environment where a program can be tested without causing any harm to the system it runs on or introducing malicious software.
When a program is run inside a sandbox, it performs its functions as if it were running on a normal system. However, anything the application wants to create or modify is lost when the program stops running, meaning it is not saved. Sandbox systems are also used to analyze and learn specific malicious software threats by examining the operation of program code.
FortiSandbox Features
The Analysis Process for Threats: Enhance your organization’s cyber defense with a two-stage sandbox approach. Suspicious and at-risk files undergo the first stage of analysis, which involves Fortinet’s award-winning antivirus engine FortiGuard, global threat intelligence queries, and code emulation. The second stage is conducted in a closed environment using system activity and behavior detection to uncover the attack’s lifecycle.
FortiSandbox Cloud can be integrated as part of FortiGate, FortiMail, FortiWeb, FortiADC, FortiProxy, FortiClient (ATP agent), and Fabric-Ready products. If an on-premises solution is preferred, it can be acquired as a virtual or physical device. Additionally, FortiSandbox is capable of integration with third-party security providers through API connections.
- Reporting: You can report and share information, including captured packets, the original file, the sandbox log, and screenshots, for analysis.
- Easy Threat Capture: Fortinet’s security products have the unique capability to integrate seamlessly with FortiSandbox, providing automatic protection with incredibly straightforward setup.
When malicious code is detected, FortiSandbox returns risk ratings. Local intelligence is shared in real-time with Fortinet products and products from other vendors you use to enhance and build immunity against new advanced threats. Optionally, local intelligence can be shared globally to help organizations worldwide through Fortinet’s threat research team, FortiGuard Labs.
FortiSandbox Integrations
FortiSandbox supports the inspection of various protocols in a unified solution by analyzing all your network traffic, simplifying your network infrastructure and operations. Additionally, it integrates with your existing security architecture, adding an enhanced threat protection layer, and it seamlessly integrates with the Security Fabric.
When configured to interact with FortiGate, FortiMail, FortiWeb, FortiADC, FortiProxy, FortiClient (ATP agent), and products from other security vendors, FortiSandbox can block suspicious content. This integration also provides these devices with timely remediation and reporting capabilities. The integration extends to other FortiSandbox units for real-time intelligence sharing, benefiting large enterprises that deploy multiple FortiSandbox units across different geographical locations.
FortiSandbox – Advanced Threat Protection
Advanced Threat Protection offers defense mechanisms against sophisticated attacks, whether known or unknown, that target sensitive data and employ malicious software techniques. It comprises components such as network devices, email gateways, systems that provide protection against malware, and central management to trigger alarms and responses in case of an attack.
Key features of Advanced Threat Management systems include early detection of attacks before they compromise critical data, rapid defense and intervention against identified threats, and mitigation of threat impact. As part of its professional services, Netsys provides FortiSandbox, which can operate on both physical and virtual machines. It serves as a proactive advanced threat detection system, capable of detecting both Zeroday attacks and known attack signatures.
FortiSwitch Secure Access Switches provide superior security, performance, and manageability for small, medium, and large-scale enterprises facing threats. They are suitable for both distributed and branch organizational structures, offering secure, simple, and scalable Ethernet switching solutions. FortiSwitch devices are fully integrated into the FortiGate Network Security Platform and the Security Fabric architecture, enabling centralized management directly through the FortiGate interface.
In summary, the FortiSwitch product family offers a solution that is user-friendly, secure, and high-performing for small, medium, and large enterprises. Its well-designed interface ensures ease of use. Below, some solutions from the product family are summarized:
FortiSwitch Products

FS-148E
FS-148E is one of Fortinet’s solutions that provide management through the FortiLink protocol. It offers superior features such as security, performance, and manageability. It is suitable for businesses of all sizes, enabling them to unify the full visibility and control of devices, ensuring the security and network access of enterprises.

FortiSwitch 108D
FortiSwitch 108D, part of FortiGate’s FortiLink solutions, stands out as a fast, easy, and secure solution on the switching side, especially for small and medium-sized enterprise structures.

FS-3032E
FS-3032E is a next-generation E-series model among FortiSwitch models, suitable for data center usage. It features 32 40GE/100GE QSFP+ / QSFP28 slots and a 6400 Gbps switching capacity, providing the highest segment performance.

FS-1048E
FS-1048E is another E-series model suitable for data center usage, featuring 48 GE/10GE SFP+ slots and a 1760 Gbps switching capacity. It includes a redundant power supply unit for uninterrupted operation.
 FS-1024D
FS-1024D
FS-1024D is part of the D-series models among FortiSwitch models, designed for data center usage. It features 24 GE/10GE SFP+ slots and a 480 Gbps switching capacity. It also includes a redundant power supply unit for continuous operation.

FS-448E-POE
FS-448E-POE is one of the new-generation E-series models in the FortiSwitch product line, with 48 RJ45 GE ports that can deliver power through the switching port (POE). It is one of the 48-port models with a 421W POE budget.

FS-448E-FPOE
FS-448E-FPOE is also from the new-generation E-series models of FortiSwitch. It features 48 RJ45 GE ports that can deliver power through the switching port (POE). Among 48-port models, it has the highest POE budget of 772W (FPOE).

FS-424E-POE
FS-424E-POE is another E-series model among FortiSwitch models, with 24 RJ45 GE ports that can deliver power through the switching port (POE). It is a 24-port model with a 250W POE budget, and it includes an additional 4 10GE SFP+ slots.

FS-424D-POE
FS-424D-POE is part of the D-series models among FortiSwitch models. It features 24 RJ45 GE ports that can deliver power through the switching port (POE). It is a 24-port model with an 185W POE budget and includes an additional 2 10GE SFP+ slots.

FS-108E
FS-108E is a FortiSwitch model designed for office use, featuring 8 RJ45 GE ports. It is a desktop-type model suitable for in-office use and includes an additional 2 GE SFP slots.

FS-108E-FPOE
FS-108E-FPOE is another model in the new-generation E-series among FortiSwitch models. It features 8 RJ45 GE ports that can deliver power through the switching port (POE). Among 8-port models, it has the highest POE budget of 130W (FPOE).
Below are Fortinet’s FortiSwitch SFP products:

FN-TRAN-SFP+GC
FN-TRAN-SFP+GC is an SFP+ type transceiver module that supports high-speed communication of up to 10 Gbps over copper lines for distances of up to 30 meters.

FN-TRAN-SFP+LR
FN-TRAN-SFP+LR is an SFP+ type transceiver module that supports long-distance communication of up to 10 Gbps over Single Mode optical fiber lines for distances of up to 10 km.

FN-TRAN-GC
FN-TRAN-GC is an SFP type transceiver module that supports communication over copper lines for distances of up to 100 meters.

FG-TRAN-QSFP+SR BIDI
FG-TRAN-QSFP+SR BIDI is a QSFP+ type transceiver module that supports communication over Multi-Mode optical fiber lines for distances of up to 100 meters at speeds of up to 40 Gbps.
What is Secure SD-Branch?
Digital transformation is fundamentally changing the way organizations conduct their business. To seize new digital business opportunities, it’s essential to ensure the security of all network components and make them compatible with each other. SD-Branch is an architecture for branch networks that either replaces or complements existing branch network systems. This solution provides agility in remote and branch office environments using a centrally controlled unified platform.
To address the challenges of today’s distributed enterprise structures, Fortinet offers a comprehensive Secure SD-Branch solution, allowing customers to merge security and network access. This extends the scope of Fortinet’s Security Fabric down to the branch level. Fortinet’s Secure SD-Branch solution encompasses FortiGate Next-Generation Firewall, FortiNAC Network Access Control, FortiSwitch, and FortiAP Access Points solutions. This solution brings benefits in the following areas:
Edge Network Protection: FortiGate’s next-generation firewall solution extends to the access layer through FortiSwitch and FortiAP. This consolidation of security and network access intersection provides an ideal architecture for Secure SD-Branch deployment. New WiFi 6 FortiAP Access Points offer increased capacity and data volume to meet growing bandwidth needs. New multi-gigabit FortiSwitch switches provide high power for even the most power-hungry Internet of Things devices.
Device Edge Protection: FortiNAC Network Access Control solution provides automatic recovery, classification, and security for IoT devices as soon as they enter the network. The new FortiNAC 8.6 version enhances anomaly detection by leveraging FortiGate as a sensor, allowing traffic scanning without the need for additional hardware at the branch.
Integrated Security: FortiGate delivers next-generation firewall services to the access layer through the integration of wireless network and switch management. Acting as a sensor for FortiGate, it provides network access control, improving discovery and visibility, and enabling the detection of security anomalies on corporate branch devices.
Ease of Management: Simplified setup and integrated management via a single unified interface streamline branch deployments. The flexible architecture can scale to support branches of various sizes.
Lower Total Ownership Cost: Fortinet’s Secure SD-Branch solution offers cost savings by not requiring any licensing fees or the purchase of network traffic sensors. Additionally, the solution simplifies management operations, reducing both time and costs, with fewer interfaces to learn and manage daily.
With the Secure SD-Branch solution, Fortinet empowers customers to easily manage their distributed branches by ensuring security stability and extending their reach down to the access layer beyond SD-WAN.
SecOps, or security operations teams, are increasingly facing more destructive and less predictable advanced cybercrimes with an expanding attack surface due to hybrid IT architectures. The shortage of skilled human resources due to the cybersecurity skills gap is another challenge.
FortiNDR is a solution used to identify and mitigate cyber threats based on abnormal network activity through a Network Detection and Response (NDR) approach. It leverages machine learning and deep neural networks (next-generation artificial intelligence). FortiNDR utilizes artificial intelligence algorithms to detect cyber threats and respond rapidly while also being capable of identifying new network activities.
Supported by purpose-driven machine learning, deep learning, pragmatic analytics, and advanced artificial intelligence technologies, FortiNDR automatically detects abnormal network activities and responds to them to mitigate security issues. This solution enables security teams to transition from a reactive security posture to a proactive one, with native integrations within the security fabric.
Additionally, FortiNDR provides coordinated responses to minimize the impact of discovered threats in addition to native integrations with Fortinet Security Fabric. It also includes API integrations with third-party solutions.
With the FortiNDR solution, Fortinet delivers AI-supported full lifecycle network protection, detection, and response capabilities.
Signs of advanced cyberattacks are detected, and FortiNDR utilizes self-learning artificial intelligence capabilities, machine learning, and advanced analytics to build a complex foundation for understanding normal network activities. It also identifies anomalies that could indicate cyberattacks. Through profile creation, it can base its analysis on factors such as IP/Port, Protocol/Behavior, Target, Packet Size, Geography, Device Type, and more.
Virtual Security Analyst: FortiNDR includes a Virtual Security Analyst (VSA) designed to simplify the intensive tasks of human analysts. It uses deep neural networks, a next-generation artificial intelligence, to analyze and detect the spread of malicious code generated by malicious traffic. VSA is pre-trained with over six million malicious and benign features, enabling it to analyze all malicious activity, accurately identify the initial point of attack, and the lateral movement of multi-variable malicious software.
Protecting web applications and APIs against DDoS attacks and malicious bot attacks is one of the critical aspects for important applications. Simultaneously, conducting security scans on web applications to identify security vulnerabilities before hackers, leveraging advanced machine learning-supported features, enhances security and reduces the management burden. Additionally, threat detection based on anomaly detection, API discovery and protection, bot mitigation, and advanced threat analytics are crucial capabilities in web application security.
FortiWeb is a web application firewall (WAF) created by Fortinet for web applications. FortiWeb safeguards all critical business applications against all types of security vulnerabilities, whether known or unknown.
The attack surfaces faced by web applications are rapidly evolving, and the attack surface changes when you update existing applications or introduce new web APIs. FortiWeb provides a solution for all these challenges. It uses a multi-layered and correlated detection approach to protect applications against known security vulnerabilities and zero-day threats. FortiGuard Labs’ Web Application Security Service keeps your applications safe by providing information based on security vulnerabilities, bots, suspicious URLs, data models, and custom heuristic detection engines.
Moreover, FortiWeb offers a service that automatically detects malicious web traffic thanks to its machine learning capability. It can detect potential unknown zero-day attacks in real-time in addition to identifying known attacks, providing real-time protection for web servers.
FortiWeb’s WAF solution offers advanced features that protect web applications and APIs against known and zero-day threats. With its advanced multi-layered approach, FortiWeb offers protection at the OWASP Top 10 level and beyond.
FortiWeb’s HTTP security firewall and denial of service (DoS) attack prevention protect web applications from attacks. It provides two-way protection against complex threats such as SQL injection and cross-site scripting (XSS) attacks. Additionally, it enables organizations to defend against threats like identity theft, financial fraud, and corporate espionage.
FortiWeb also provides the tools necessary for adhering to PCI DSS firewall and patch requirements, industry regulations, best practices, and internal security policies.
FortiWeb can enhance the security of your critical applications with services such as:
Security vulnerability scanning and patching.
IP reputation, web application attack signatures, credential stuffing defense, antivirus, and FortiGuard-supported FortiSandbox Cloud.
Real-time attack forecasting and reporting with advanced visual analysis tools.
Integration with FortiGate and FortiSandbox for ATP detection.
Behavioral attack detection.
Advanced avoidance of false positives and negatives.
FortiWeb offers both hardware and virtual machine platforms, providing services for medium and large enterprises as well as service providers.
FortiWeb is a security firewall designed especially to protect web servers. It offers application layer threat detection and protection services for HTTP and HTTPS services, including:
1. Microsoft IIS
2.Microsoft SharePoint
3. Apache Tomcat
4. Nginx
5. JBoss
6. IBM Lotus Domino
7. Microsoft Outlook Web Application (OWA)
8. RPC and ActiveSync for Microsoft Exchange Server
9. Joomla
10 .WordPress
With FortiWeb WAF solution and FortiWeb ML (Machine Learning), it provides strong protection without the need for time-consuming manual configurations required by other solutions. With ML, FortiWeb identifies abnormal behaviors and distinguishes between malicious and benign anomalies. In other words, it has bot reduction capabilities that prevent malicious bot activity while allowing legitimate bots to connect.
In addition to the application layer firewall, FortiWeb can also provide load balancing services:
- Secure HTTP/HTTPS applications
- Prevention of tampering and reverse
- Improvement of application stability
- Monitoring servers for downtime and connection load
- Reduction of response times
- Acceleration of SSL/TLS
- Acceleration of compression
- Simultaneous rewriting of content
Cyber Threat Intelligence (CTI) is a critical component of cybersecurity, involving the collection, analysis, and interpretation of information about potential threats targeting an organization’s digital infrastructure. CTI is a vital process for identifying and understanding potential cyber threats that can pose a risk to an organization, gathering data from various internal and external sources.
As cyber attacks become increasingly complex and the digital environment expands, organizations face significant challenges in understanding and mitigating potential risks. As digitalization becomes inevitable, organizations’ digital footprints grow exponentially, necessitating accurate identification and effective protection of the cyber attack surface.
In this context, Netsys offers cyber threat intelligence and next-generation digital risk protection services utilizing Fortirecon. By using Fortirecon, organizations can continuously monitor their external attack surface, identify brand risks, and respond to threats more quickly and effectively. Fortirecon combines machine learning, automation, and human intelligence to provide this service.
Fortirecon is a powerful combination of learning machines, automation capabilities, and the expertise of FortiGuard Labs, creating a Digital Risk Protection Service (DRPS) that helps organizations manage risk by protecting their brand reputation, corporate assets, and data. This service enables organizations to effectively defend against attacks in the initial discovery phase, providing comprehensive protection across External Attack Surface Management (EASM), Brand Protection (BP), and Attacker-Centered Intelligence (ACI).
As a threat intelligence solution, Fortirecon offers companies consistent and comprehensive services in three main areas:
- External Attack Surface Monitoring: Helps organizations understand their risk profiles and reduce risks early on. It identifies exposed corporate assets and associated security vulnerabilities, both known and unknown, and prioritizes the remediation of critical issues by understanding how the organization and its affiliates appear from both inside and outside.
- Brand Protection: Assists organizations in protecting their brands and identifying risks to their customers. It detects common techniques used by cyber threat actors, including web-based typos, compromised content, identity theft incidents, credential leaks, and impersonation on social media.
- Attacker-Centered Intelligence: Enhances the security awareness of Security Operations Center (SOC) teams by providing sector and geography-specific coverage, helping organizations better understand attackers and protect their assets.
With these services, Fortirecon strengthens the cybersecurity posture of organizations, making them more prepared against threats.
As digital transformation increases the attack surface, security management becomes more complex. Cybersecurity teams struggle with the volume of alerts generated by numerous systems, networks, and security devices.
One of today’s crucial needs is securing the infrastructure, applications, and endpoints (including IoT devices). This requires real-time visibility of all devices and infrastructure. Organizations need to know which devices pose a threat and their location. Security Information and Event Management (SIEM) Solutions analyze event data in real-time, enabling early detection of data breaches and targeted attacks.
FortiSIEM combines visibility, correlation, automated response, and remediation in a single scalable solution. It reduces the complexity of managing network and security operations, enhancing breach detection and even prevention. It offers the ability to collect and analyze data from various information sources. FortiSIEM integrates traditional methods of security operations centers (SOC) and network operations centers (NOC). FortiSIEM UEBA detects behavioral deviations based on machine learning and statistical methods, adding actionable insights. FortiSIEM UEBA consolidates telemetry data from endpoint sensors, network device flows, server and application logs, and cloud APIs, creating comprehensive profiles for users, peer groups, endpoints, applications, files, and networks. Its behavioral anomaly detection provides end-to-end effectiveness and visibility, achieved cost-effectively.
Features and Advantages of FortiSIEM
FortiSIEM offers advanced threat protection and high business value beyond just collecting security events. Key features include:
- Scalable Architecture and Licensing: Its VM architecture and licensing options offer rapid scalability. Adding VMs easily increases performance and log processing capacity.
- Centralized Management and Control: Access most FortiSIEM features via an intuitive, web-based GUI. Customizable role-based access control and integrated CMBD for asset discovery and management enhance this feature. Performance and availability monitoring expand the platform.
- Ready-to-Use Compliance Reports and ROI: Improves efficiency and reduces risk. FortiSIEM’s ready-to-use Compliance Reports help organizations stay compliant. Predefined content shortens the time to value. Security teams can better understand the impact of incidents by defining business services. It offers reports supporting a wide range of compliance audit and management requirements.
- Automated Incident Reduction: When a threat is detected, an automatic script can be run to reduce or eliminate the threat. These scripts support various devices and can perform a wide range of actions.
- Performance Monitoring: Monitors basic system/common measurements. Provides monitoring for virtualization, storage usage, Microsoft Active Directory, databases, VoIP infrastructure, and more. Allows the addition of custom metrics.
- Availability Monitoring: Monitors system up/down status and provides analysis, critical interface and service monitoring. Models service availability with synthetic transaction monitoring and calculates SLAs.

Identify and block attacks that other WAFs may overlook.
Protect applications with behavioral analytics, layer 7 DDoS prevention, application-layer encryption of sensitive data, threat intelligence services, and API security.
Application Layer Attacks: Can bypass signature and reputation-based security solutions.
Web Application and API Attacks: Rapid adoption of APIs (e.g., GraphQL APIs, OWASP Top 10) has led to new application attack surfaces and increased threat thresholds.
Security Automation for DevOps: Delivers applications to the market faster and at lower cost while ensuring higher security effectiveness.
Targeted Attack Campaigns: Active attack campaigns can be challenging to detect compared to individual attacks.
Automated Attacks and Bots: Automated attacks and bots can overwhelm application resources.
Credential Theft: Attacks that steal application credentials or take advantage of compromised accounts.
Flexible deployment and management options tailored to your needs;
BIG-IP Advanced WAF identifies and mitigates attacks that other WAFs may overlook. It offers a specialized, dynamic control panel that ensures compliance with threats listed in the OWASP Top 10. It enhances directed configurations, learning engines, and the ability to create customized policies for common WAF use cases. It also supports detailed security policies for microservices and APIs.
More Than Load Balancing!
BIG-IP LTM software ensures the availability of applications for users by distributing all types of traffic requests across applications using both static and dynamic load balancing, eliminating single points of failure. By employing load balancing for both static and dynamic content, BIG-IP LTM can help your organization maintain application high availability and reliability across various scenarios.
Load Balancing: Increases availability by distributing application load across multiple servers and clouds.
Traffic Steering: Directs traffic of a specific type to resources designed to handle that workload.
Health Monitoring: Verifies the health and performance to check the status of applications and resources.
Enhance End-User Experience with BIG-IP LTM!
Nobody likes a slow and unreliable application. BIG-IP LTM dramatically scales to meet traffic demands, improving load times and user experiences. Additionally, it makes real-time protocol and traffic management decisions based on application and server conditions, allowing you to take control with rule customization and programmatic control.
TCP Optimization: Enables cutting-edge optimization to dramatically enhance mobile performance.
Caching: Improves performance and scalability by fetching repetitive traffic from application servers.
Emerging Protocols: Provides load balancing support for IoT clients via the MQTT protocol.
Secure Your Customers’ Data!
BIG-IP LTM delivers industry-leading SSL performance and visibility for inbound and outbound traffic, allowing you to protect your entire user experience by encrypting everything from the client to the server. It also establishes defenses against DDoS attacks and offers ICAP services for data loss protection and virus protection integration.
Data Protection: Encrypts traffic with optional cipher suites based on policy, compliance, or mobile needs.
Perfect Forward Privacy: Preserves customer privacy with a unique key for each session, protecting it from future decryption.
Key Protection: Protects and manages keys with hardware security modules for physical, virtual, and multi-cloud deployments.
Real-Time Business Insights!
You want to know how your applications and network perform for users at all times. BIG-IP LTM brings data recording and analysis, real-time health monitoring, and detailed F5 analytics at your fingertips. This can help you maintain and enhance application performance.
F5 Analytics: Offers detailed tracking for applications, which can be used for performance analysis.
High-Speed Logging: Processes logging messages and sends them to remote high-speed logging servers for reporting.
Detailed Analysis: Exports data streams for third-party analytics, providing detailed searching and troubleshooting.
Comprehensive Protection Against a Broad DDoS Attack Spectrum!
BIG-IP DDoS Hybrid Defender provides advanced cloud and on-premises Distributed Denial of Service (DDoS) defenses to offer real-time protection against volumetric DDoS threats. It effectively prevents sophisticated Layer 3 and Layer 4 volumetric attacks and successfully handles Layer 7 attacks when necessary.
Multi-Layer Defenses: Offers deeper defense against complex network attacks and sophisticated application attacks.
Comprehensive Protection: Enables full SSL decryption, anti-bot capabilities, and advanced diagnostic methods in a single solution.
Unmatched Performance: Provides the highest performance with line-rate capabilities without affecting traffic.
API Gateway Protection!
API Gateways do not just need the ordinary DDoS protections at L3 and L4. To ensure that an API Gateway does not fall victim to a DoS attack, an extremely fast L7 Behavioral DoS solution is required to detect threats almost in real-time, create sophisticated signatures that can be applied to custom software, and even provide hardware-based DDoS protection at line rate, even in environments exceeding 100 Gbps.
Behavioral DoS: Creates dynamic signatures to allow faster and more precise threat identification in addition to standard security signatures.
Line-Rate Blocking: Operates in inner or outer band mode with sub-second attack detection, geographic tracking, smart signaling, and hardware assistance.
Advanced Blocking Techniques: Offers configurable rate limiting, blocking, connection limiting, resource limiting, and more.
Mitigating Zero-Day DDoS Vectors with Protocol Attack Detection!
DDoS attacks are rapidly evolving in terms of intensity, complexity, and sophistication, threatening businesses with revenue loss, customer trust erosion, and industry reputation damage. How quickly your organization can detect and mitigate these threats is critical for ensuring service continuity and limiting damage.
DoS and DDos Protection: Delivers the best in reliability, resilience, and scalability with a stateless solution.
Protocol Anomaly Detection: Gathers data to understand ‘normal’ system and network behavior, creating a foundation to adapt to application changes.
Automatic Signaling: Routes to scrubbing solutions with automatic signaling based on threshold-based automatic signaling for volumetric attack mitigation.
Mitigating Zero-Day DDoS Vectors with Protocol Attack Detection!
Effectively mitigating L7 attacks requires inspecting L7 attacks, especially when dealing with HTTPS-based L7 attacks. Since the majority of volumetric attacks occur at Layer 3 and 4, these are easily detectable and mitigable. However, when L7 attacks occur over HTTPS, SSL/TLS decryption becomes critical. SSL/TLS decryption can be enabled in seconds, providing the necessary visibility to make decisions on how to mitigate an attack or attack campaign.
SSL/TLS Decryption: Enhances visibility of SSL traffic for effective mitigation of application layer attacks.
Proactive Bot Defense: Defends against malicious bot activity before attacks.
Purpose-Built: Designed to provide an integrated solution for L3-7 protection, DDoS mitigation, and SSL/TLS decryption without affecting legitimate traffic.
Hybrid Deployment and Automatic Signaling!
BIG-IP DDoS Hybrid Defender offers deeper defense. It is the only multi-layer defense solution that provides protection against complex application attacks and sophisticated network attacks. It also delivers full SSL decryption, anti-bot capabilities, and advanced diagnostic methods in a single solution. Moreover, it ensures the highest performance with line-rate capabilities without affecting legitimate traffic. BIG-IP DDoS Hybrid Defender can be deployed on B4450, i15x00, r10000 devices, and soon on SmartNICs.
Zero Trust Application Access!
Deploys detailed context-based zero trust model validation for every application access request.
Identity-Based Proxy: Provides secure access to applications by offering a detailed approach to user authentication and authorization, allowing access only with context and identity awareness in each request.
Single Sign-On (SSO) and Access Federation: Integrates with existing SSO and identity federation solutions, offering access with a single login, regardless of whether the user’s applications are SAML-compliant or not.
OAuth 2.0 and OIDC Support: Simplifies access authorization from trusted third-party identity providers like Google, LinkedIn, Okta, Azure AD, and others, enabling social login.
Robust Endpoint Security!
Controls device security and integrity without user intervention and provides VPN access for every application.
F5 Access Guard: A browser-based extension that works in coordination with APM to provide continuous device health checks.
Enhanced Identity Verification: Supports additional identity verification types (e.g., multi-factor authentication (MFA)) when the nature of the device location or application data requires more analysis.
Mobile Device Management Integration: Integrates with leading MDM and Enterprise Mobility Management (EMM) solutions, including VMware Horizon ONE (AirWatch), Microsoft Intune, and IBM MaaS360.
Secure Remote Access!
Obtains highly customized identity verification and access control for individual applications, networks, and resources with end-to-end data encryption.
Per-App VPN: Provides detailed control over corporate network access by ensuring that data transmitted by managed applications is only sent through a separate VPN tunnel.
Visual Policy Editor (VPE): Offers an advanced graphical interface to design and manage detailed access control policies on an individual or group basis quickly and easily.
Access Guided Configuration: Utilizes a single and user-friendly interface to deploy your legacy applications tailored to your organization and Azure AD Conditional Access policies.
Hybrid Application Access!
Enables centralized identity verification for all applications by integrating with Identity and Access Management Services (IDaaS) providers such as Azure AD.
Identity-Based Proxy: Provides secure access to applications by offering a detailed approach to user authentication and authorization, allowing access only with context and identity awareness in each request. IAP enables access tailored to each request context and identity awareness.
Azure AD Conditional Access Integration: Easily deploys Conditional Access policies using BIG-IP APM’s Access Guided Configuration (AGC).
Integration with Third-Party Risk Assessment Engines: Use third-party User and Entity Behavior Analytics (UEBA) and risk engines via the API Connector for informing policy-based access controls to enhance security further.
Accurate Driver Detection with Behavioral Analysis!
BIG-IP AFM, certified by the ICSA Labs as a firewall, provides precise threat detection with machine learning, stress monitoring, dynamic signatures, and attack prevention.
Machine Learning: BIG-IP AFM learns normal traffic baselines and begins collecting data to understand the “normal” systemq and network activity.
Stress Monitoring: It detects abnormal server stress and monitors the health of the protected server. When the server shows signs of stress based on deviations from normal network activity, interventions are initiated.
Dynamic Signatures: BIG-IP AFM recognizes malicious traffic and actors. Signatures are quickly created specific to the threat source and are ready for deployment before impacting service.
Attack Prevention: Dynamic signatures are applied. The health of the server is continuously monitored as an intervention measure, and additional signatures are created as needed until the attack is sufficiently addressed.
Achieve Consistent Security and Effective Visibility!
BIG-IP AFM is a fundamental component of F5’s application protection solutions, integrating four key security elements: firewall, DDoS mitigation, DNS security, and application attack protection systems (IPS).
These solutions can be consolidated onto a single BIG-IP platform, reducing management complexity and costs while delivering superior performance and scalability.
Consistent Protection for Containerized Applications: Protect container-based applications regardless of platform or location with attack detection and mitigation services.
Actionable Reporting and Visibility: Easily understand your security posture with customizable rich telemetry to provide insights into all types of incidents and enable effective forensic analysis.
Ensure Network Availability, Security, and Scalability!
Protecting network resources without compromising flexibility and controlling costs is an ongoing challenge. BIG-IP AFM enables service providers to protect both the network and subscribers with unique subscriber aggregation capacity while consolidating network infrastructure and flexibility without compromising them.
Protection with Full Proxy Capabilities: Control all incoming subscriber connections and server-client responses based on security and protocol parameters and mitigate threats based on them before forwarding.
Inspect SSL Sessions: Decrypt SSL traffic at high speed and efficiency to detect hidden attacks.
Automate Security Deployment: Use a single and user-friendly interface to design security policies based on services and protocols and configure them with an effective rule and policy graphic interface.
From Network Core to Edge, Defend and Protect Your Services
BIG-IP AFM is a high-performance, full proxy network security solution designed to protect against threats entering networks over the most widely deployed protocols. The unique application-centric design of this product provides more effective protection against targeted network infrastructure level attacks. With BIG-IP AFM, organizations also gain protection from over 100 attack signatures with more hardware-based signatures than other leading firewall providers and achieve superior programmability, compliance, and visibility for threat conditions.
Secure, Simplify, Centralize
F5 BIG-IP Access Policy Manager (APM) secures, simplifies, and centralizes access to all applications, APIs, and data, providing a secure and user-friendly access experience regardless of user location or where applications are hosted.
BIG-IP APM is available in all business models, including perpetual licenses, subscriptions, the general cloud market, and ELAs.
Scalability, Security, and DNS Optimization
Unmatched DNS Performance!
Handle hyper-scalability of up to 100 million responses per second (RPS) for DNS queries to manage rapid increases in DNS queries. With a feature set that includes multi-core scalability, DNS Express, and IP Anycast integration, DNS distribution can process millions of DNS queries and ensure the best application performance for users.
100M RPS Performance: BIG-IP DNS hyper-scales authoritative DNS up to 100 million query responses per second (RPS), ensuring users connect to the best site and supporting optional scalability for DNS and global applications. DNS Express enhances standard DNS functions by taking over DNS responses and scaling to up to 50 million RPS, improving DNS functions.
Optional Scalability for DNS: Deploy optional scalability to BIG-IP DNS and GSLB with speed and object limit capacity limits.
Cloud and On-Premises Global Performance: Route users to servers that offer the fastest and most reliable connection based on business policies, user locations, and application/server performance.
Secure DNS Is Critical!
Comprehensive security is required for every application because applications are the focus of both malicious actors and legitimate users. A poorly secured network can be costly in terms of customer and revenue impact. BIG-IP DNS services provide flexibility that is friendly to DevOps along with the scale, security depth, and investment protection needed for both traditional and emerging applications.
DNS Firewall/DDoS: Combines with BIG-IP AFM to protect DNS from volumetric DDoS attacks such as UDP flood attacks or amplification DDoS attacks.
DNSSEC: Protect LDNS servers from cache poisoning and man-in-the-middle attacks with real-time DNSSEC.
DoH/DoT: Decrypt DNS queries over HTTPS (DoH) without impacting RPS and ensure DNS requests and responses over TLS (DoT) are not tampered with through man-in-the-middle attacks.
Enhance Caching and Resolution for Increased Scalability!
DNS delay can be reduced on BIG-IP DNS by enabling a DNS cache, allowing it to respond immediately to customer requests. This consolidates the cache and increases cache hit rate, reducing DNS delay by up to 80%. In addition to caching, BIG-IP DNS allows for its own DNS resolution without using upstream DNS resolution.
Cache Consolidation: Reduces latency and response time by up to 80%.
DNS Load Distribution: IP Anycast integration distributes DNS request load and directs single IP requests to multiple local devices.
Location-Based Routing: Route users to the nearest data center with geographic location-based load balancing for the best user experience.
Simplify DNS Network Management!
Networks are growing both in scale and traffic demands, resulting in increased availability for users and better access and management requirements for administrators. BIG-IP DNS provides easy visibility and programmability to ensure easier maintenance of network architectures.
Integration with Existing Infrastructure: Communicate with network devices to diagnose network endpoint health and integrate with network devices such as SNMP agents, third-party caches, servers, routers, and load balancers.
Flexible Site Options: Enable flexible site options, including Active/Active, Active/Passive, or Active/DR.
Seamless Failover for Continuous Access: Provide seamless failover for all data centers or individual applications/servers to ensure users have uninterrupted access to the applications they need.

Arista, viewing quality as the top priority rather than an option, has a presence in the Turkish market with its experienced engineers worldwide. Arista made its first production after 4 years of its establishment with the idea of how to do better and what to do differently.
It introduces the SYSDB working principle to products, where the interruption status of agents on the system does not affect each other and guarantees maximum uptime with its self-healing feature. It provides solutions suitable for its customers’ problems and network traffic with the deep-buffer, shallow buffer, and ultra-low latency products it produces. In addition to the standard CLI, it provides device management at the Linux layer, and with API support, it significantly reduces operational burden with the Cloud Vision central management tool.
With this centralized system management, it also provides the opportunity for BIG-DATA by bringing the Real-Time Telemetry feature in addition to traditional SNMP traffic, enabling precise analysis. It offers integration opportunities with manufacturers such as Fortigate, Palo Alto, VMWare, Openstack, Ansible, Puppet, etc. It stands out in DC interconnect solutions with VXLAN and Active-Active DC designs. It creates an advantage in terms of cost compared to its competitors with its WI-FI solutions offered without the need for an Arista controller. It also allows the management of APs on the Cloud Vision central management tool.
A switch that carries the maximum load between multiple switches can be described as a unit. This type of switch is also known as a backbone switch. In its simplest form, a backbone switch is responsible for load sharing between switches and consolidating all the load.
The most significant advantage of a Backbone Switch is having high-speed links and connections that create the primary pathways on the network. Thanks to the WAN, it facilitates the connection of Edge Switches that cannot connect to desktop computers or other end-user terminals.
A backbone plays an effective role in connecting various network components that provide different data exchanges within a computer network. Success can be achieved by connecting different networks in the same building, different buildings, or wide areas with a Backbone Switch. The capacity of a Backbone Switch is generally higher than the connected networks.
In a Backbone Switch system, predictability can be achieved in some cases related to latency. With this switch system architecture, you can always control the number of stops each data packet needs to travel. As a result, the Backbone Switch makes management and sustainability easier.
In the old system, the load coming from a server had to go through several stages before communicating with a different server on the same network. These journeys involved passing through several switches. With the support of the Backbone Switch, a more stable structure is established, which helps prevent bottleneck formation.
An Edge Switch is defined as a network device that facilitates communication between connected computers. These devices can be computers, other network hardware, and printers, among others. To establish communication, an Edge Switch is connected to a network card via a cable. The Edge Switch communicates based on MAC addresses. Using the MAC address table (CAM table), the switch records the MAC addresses and IP addresses of computers on the network.
If the MAC address of the destination computer is registered in the MAC table, when a connection request arrives from the source computer to the destination computer, the switch notifies the destination computer. If the MAC address of the destination computer is not registered in the table, the switch broadcasts the request to all other computers except the source computer. Through this process, the MAC address of the destination computer is recorded in the MAC table.
Switches are commonly used in data centers, offices, systems employing network products, and businesses. These devices allow two or more computers to communicate with each other and work on the same file. They can transmit data based on the device connected to their ports. Typically, Edge Switches operate architecturally through Backbone Switches.
A switch is referred to as a network hardware that facilitates communication between all connected devices. On the other hand, a Backbone Switch emerges as the unit where most of the load is located among multiple switches. In terms of their fundamental duties and functions, these two switches have different features. Accordingly, the primary task of a Backbone Switch device is to distribute the load among switches or collect all the load, while an Edge Switch plays an active role only in communication between devices.
A switch is referred to as network hardware that facilitates communication between all connected devices. On the other hand, a Backbone Switch emerges as the unit with the most load among multiple switches. In terms of their fundamental duties and functions, these two switches have different features. Accordingly, the primary task of a Backbone Switch device is to distribute the load among switches or collect all the load, while an Edge Switch plays an active role only in communication between devices.
A Router device has multiple interfaces through which it receives data packets. It evaluates the network addresses of incoming packets and decides which interface to forward the packet to. To make this decision, it uses the local routing table. These tables map out a path from one point to another for sending data, and the transmission is carried out accordingly.
Access Points are devices found in wireless networks that allow clients to connect wirelessly and access the internet. They facilitate the connection of wireless network clients (such as phones, tablets, laptops, etc.) to each other and to the network, managing wireless network traffic.
Access Points are typically used as access points in wireless networks. These devices provide internet access by connecting to a wired network or a device like a modem/router. Access Points can also be referred to as ‘Hotspots’ and are used to provide public wireless networks. The performance of Access Points may vary depending on environmental factors, network congestion, and the device’s capabilities.
When it comes to Access Point models, there are many advantages in terms of usage. Access Point technologies provide functional benefits to businesses in addition to possibilities like enhancing connection performance. The general categories of advantages in using Access Points can be detailed as follows:
- Abstraction from Complex Wired Connection Infrastructures
- Cost-Effective Connection Solutions with Access Point
- With the help of an Outdoor Access Point, internet access can be provided in open areas and over a wide area.
- It helps reduce costs by reducing the number of modems in large-scale accommodation areas such as companies, student dormitories, or hotels, and so on.
Arista’s CloudVision CUE solution provides network administrators with the tools required to ensure the seamless operation of the Wi-Fi network, proactively detect issues that may adversely affect the user experience, test the network on demand and based on predefined schedules, and ultimately deliver actionable insights. The primary objectives of CloudVision CUE are to ensure the optimal performance of the deployed Wi-Fi network and achieve the shortest ‘mean time to resolution’ in case of any reported issues, should users experience anything less than the seamless application experience they expect.
Arista’s CloudVision CUE solution leverages the power of the cloud and vast data sets within the customer base to continuously apply supervised and unsupervised learning concepts in deciphering the user application experience. Arista uses inference models to quickly reach the root cause of any poor experience and proactively provide this information to network administrators along with recommended remedies.
The distributed control plane of Arista’s CloudVision CUE solution enables seamless and unlimited scalability, eliminates single points of failure, and delivers an excellent user experience. With the best hardware in its class, including the latest Wi-Fi 6 AP family, Arista’s CloudVision CUE is the solution that provides the best value for Enterprise Campus deployments with industry-leading Wireless Intrusion Prevention System and robust Guest Management and Analytics solutions. The all-inclusive licensing policy of CloudVision CUE ensures that customers can enjoy all the benefits of this top-notch solution without the fear of missing out.
CloudVision Portal (CVP) is a web-based GUI for the CloudVision platform.
The portal provides a turnkey solution for automating network operations, including tasks such as network device provisioning, compliance, change management, and network monitoring. It communicates southbound with Arista switches through eAPI and has open standard APIs northbound for integration with third-party or in-house service management packages.
An overview of CloudVision Portal (CVP) positions CloudVision as the network control point between the physical infrastructure (network layer) and the service management layer.

SSL VPN, genel olarak Pulse Connect Secure – Ivanti Connect Secure, kuruluşların ağ kaynaklarının gizliliğini, bütünlüğünü ve kullanılabilirliğini korumalarına yardımcı olurken çalışanların ve yetkili kullanıcıların uzaktan çalışmasına veya harici konumlardan kaynaklara erişmesine olanak tanıyan sağlam ve güvenli bir uzaktan erişim çözümü sunar.
Neden ihtiyaç duyulabilir?
Secure Remote Access: PCS – ICS, kullanıcıların dizüstü bilgisayarlar, akıllı telefonlar veya tabletler gibi çeşitli cihazları kullanarak herhangi bir yerden kuruluşlarının ağına güvenli bir şekilde bağlanmasına olanak tanır.
Enhanced Security: PCS- ICS, VPN bağlantısı üzerinden iletilen verilerin gizliliğini ve bütünlüğünü korumak için çeşitli güvenlik önlemleri kullanır.
Granular Access Control: PCS – ICS, yöneticilerin ağ içindeki belirli kaynaklara kimlerin erişebileceğini belirleyen ilkeleri tanımlamasına ve uygulamasına olanak tanıyan ayrıntılı erişim denetimi mekanizmaları sunar.
Multi-Factor Authentication (MFA): Güvenliği daha da artırmak için PCS, kullanıcıların basit bir kullanıcı adı ve parolanın ötesinde ek kimlik bilgileri sağlamasını gerektiren çok faktörlü kimlik doğrulamayı destekler.
Centralized Management: PCS – ICS, yöneticilerin VPN altyapısını etkin bir şekilde yapılandırmasına ve izlemesine olanak tanıyan merkezi bir yönetim arabirimi sağlar. Bu, kullanıcı hesaplarını yönetmeyi, erişim ilkelerini tanımlamayı, ağ trafiğini izlemeyi aynı zamanda denetim ve uyumluluk amaçları için raporlar oluşturmayı içerir.
Scalability and Flexibility: PCS – ICS, çeşitli BT altyapılarını barındırmak için donanım araçları, sanal araçlar ve bulut tabanlı çözümler dahil olmak üzere esnek devreye alma seçenekleri sunar.
Integration with Existing Infrastructure: PCS – ICS, kimlik doğrulama sunucuları, güvenlik duvarları ve diğer güvenlik araçları dahil olmak üzere çok çeşitli mevcut BT sistemleriyle entegre olur. Bu entegrasyon, kuruluşların güvenlik altyapısındaki mevcut yatırımlarından yararlanmalarına ve VPN çözümünün dağıtımını kolaylaştırmalarına olanak tanır.
NAC, bir kuruluşun ağına bağlanan cihazlar için uç nokta uyumluluğunu ve güvenli ağ erişimini zorlamak için tasarlanmıştır.
Neden ihtiyaç duyulabilir?
Endpoint Compliance = Pulse Policy Secure – Ivanti Policy Secure, ağa bağlanmaya çalışan uç noktalarla kuruluşun güvenlik politikalarına uymasını sağlar. Virüsten koruma yazılımının, işletim sistemi yamalarının, güvenlik duvarı ayarlarının ve diğer güvenlik yapılandırmalarının varlığını ve durumunu doğrulamak için bağlantı öncesi ve bağlantı sonrası kontroller gerçekleştirir. Bu, yetkisiz ve potansiyel olarak savunmasız cihazların ağa erişmesini önlemeye yardımcı olur.

Citrix Virtual Apps and Desktops
Citrix Virtual Apps and Desktops (Application and Desktop Virtualization) is a technology that allows access to virtual operating systems running on central servers from various types of devices, making applications and desktop environments available. This technology enables users to access the operating systems and applications they use in a corporate environment from any location and with any device, ensuring security and the same speed and experience. Users only need to install the Citrix Workspace (Receiver) client application on the devices they will use for access. Since applications and desktop environments are hosted on central servers, users are not tied to specific devices, and in case of issues with their devices, they can continue their work from where they left off using a different device.
DaaS and VDI Solutions for Hybrid Work Environments
As a leading provider of DaaS (Desktop as a Service) and VDI (Virtual Desktop Infrastructure), Citrix offers the capabilities you need to deliver virtual applications and desktops to employees. Through DaaS – Desktop as a Service (Cloud) technologies, organizations reduce downtime, enhance security, and alleviate many of the challenges associated with traditional desktop management.
Today’s employees work from different locations rather than local company offices, which is why companies need to rethink and plan how IT services are delivered. Some companies turn to desktop service (DaaS) solutions to improve their physical desktop strategies, while others upgrade their on-premises virtual desktop infrastructure (VDI) and evaluate cloud options. By managing on-premises resources alongside cloud workloads, you can achieve the best of both worlds without losing your existing data center investments. With DaaS (Cloud) technology, data is securely stored in the cloud or in a data center, not on devices. Therefore, end users can work securely from any device, any location, and any network. Additionally, IT, with central management advantages, can easily manage, monitor, and scale environments. Citrix DaaS is an easy-to-manage solution that allows organizations to securely deliver DaaS and VDI applications and desktops to any device, over any network. It supports a mix of cloud deployments, public clouds, private clouds, or on-premises data centers, making it an ideal choice for industries subject to strict regulations like healthcare, government, and finance. Simplified DaaS solutions allow companies that want to fully outsource their infrastructure to easily reduce infrastructure and maintenance overhead with less intervention. All of this translates to more flexibility for IT and a superior experience for your users. Virtualized applications and desktops work like their physical counterparts regardless of the device or connection type thanks to HDX technology. With comprehensive cloud security, you can continuously secure applications and data between users, devices, and networks. The result is improved security, lower costs, and increased efficiency.
Citrix VDI
When you want to keep your workloads within your corporate environment, Citrix Virtual Apps and Desktops are the right choice. Citrix makes it easy for corporate security teams or those who wish to keep data in their own data center for operational reasons. Application and desktop virtualization is done according to your preference and comes with a range of features to increase productivity and enhance security.

Superior Experience
You can provide an exceptional experience with integrated communication tools, custom engineering applications, or targeted optimizations for critical healthcare workloads, regardless of device or network conditions.
Easier Management
Whether you support 10 users or thousands of users, you can use Citrix Management Tools to troubleshoot issues, control costs, and monitor the health of your environment.
 More Secure Access
More Secure Access
Comprehensive security policies, application protections, and authentication mechanisms can keep cybercriminals away from data stored in applications.
Better BYOD
You can provide a locally operating universal client for all desktops, laptops, tablets, and smartphones without requiring extra IT work.
Long-Term Support
With Long-Term-Service-Release (LTSR) versions, you can receive continued fixes and predictable service support for up to 10 years.

Discover the Security of Passwordless Life!
Eliminating passwords has been a long-standing goal. The development and widespread use of technologies such as smartphones, fingerprint and palm readers, image and voice recognition devices, and more have been a significant step towards achieving this goal.
Established in 2013, the FIDO Alliance (Fast Identity Online) has developed new authentication standards to reduce the world’s excessive reliance on passwords. The widespread adoption of standards such as UAF, U2F, and FIDO2 (WebAuthn) has brought about passwordless authentication systems that enhance security and user experience (UX) for organizations. This, in turn, enables faster and more secure access to critical systems and data.
Eliminate Passwords.
According to Gartner, by 2023, 30% of organizations will use at least one type of passwordless authentication and eliminate static passwords. This represents a significant increase from today’s 5%.
No secrets to forget.
No writing down passwords, no OTPs.
No phishing, no sniffing.
No password reset costs.
Passwordless FIDO2 WebAuthn:
AuthTake offers FIDO support using the Public-Key Cryptography (PKC) infrastructure, a secure passwordless user authentication service.
In the FIDO workflow, the login request is initiated by the user’s device (such as a smartphone, FIDO-supported physical token, etc.). The device forwards the login request to the AuthTake server. In response, the server creates a challenge message and sends it to the device. It then signs the message using the secret key it holds and sends it back to the server. The server verifies the signed message’s authenticity with the public key it possesses, thus confirming the login.
In all these authentication processes, FIDO requests biometric authentication based on the user’s mobile device’s capabilities.
Why AuthTake?
Passwords have become a major actor in security breaches, unauthorized access, and compromised user accounts in organizations. Managing passwords and eliminating their problems leads to operations that require high costs.
AuthTake eliminates passwords, enabling organizations to increase their security levels and reduce password management costs with rapid and secure “Passwordless User Authentication” technology through Public-Key Cryptography (PKC) and FIDO infrastructure.
Advantages of AuthTake:
Provides hybrid operation with On-Prem and Cloud Active Directory support.
Offers a good user experience with fast login and easy integration. (Average login time is 3 seconds.)
Allows offline use, making it possible to log in using a PIN even in offline situations where the system is not connected.
Supports mobile FIDO2 and hardware tokens from FIDO2-supporting hardware token manufacturers such as Yubikey and Feitean.
Users can remotely lock their data, regardless of their location.
Provides unit-based deployment and access group determination with rule-based operations.
By initiating user authentication from mobile devices, it prevents attacks such as PUSH and MITM.
The single sign-on feature enables users to log in to corporate and cloud applications with a single identity and password.
By eliminating passwords, it prevents issues like forgetting, noting down, and sharing passwords.
How to Use AuthTake:
Login with Notification
The user ensures that a notification is sent to their device by only entering their username for system access. By approving the notification received through the mobile application, they grant access and log in.
Login with QR Code
To log in, the user scans the QR code on the login screen of the system they want to access using the AuthTake application on their mobile device. They perform the required biometric verification or enter a PIN.
Remote Login/Logout with Remote Control
Users can remotely log in and lock their session on the workstation they paired with their mobile device using the AuthTake application on their mobile device.
Offline Login
When there is no internet access on the computer or mobile device, users can perform user authentication by creating a PIN and logging in using the Off-line Login option in the AuthTake application.
With AuthTake, transition to fully passwordless user authentication using FIDO2, WebAuthn, and Public-Key Cryptography technologies, and eliminate shared secrets like passwords, OTPs, SMS codes, and more that are targeted by identity thieves.
PASSWORDLESS SINGLE SIGN-ON (SSO)
Faster and more secure access to all your enterprise applications with passwordless single sign-on.
Discover the Security of Passwordless Life!
Passwordless Single Sign-On (Passwordless SSO)
AuthTake allows fast and secure access to your corporate applications and cloud applications like Salesforce, Amazon, Office 365, Dropbox, DocuSign, etc., with support for SAML and OAuth protocols. This is made possible through the AuthTake Portal, which offers passwordless single sign-on support.
Users access many applications throughout the day, both locally and in the cloud. Having to perform user authentication repeatedly for each application not only results in time wasted but also makes the process cumbersome. AuthTake SSO eliminates the use of passwords for your users, enabling them to experience secure and quick access to your applications, whether they are in the cloud or on-premises. It not only saves your users time but also boosts their productivity by allowing access to multiple business applications with a single sign-on.
Application Catalog
AuthTake SSO comes with pre-installed web applications and continues to add new applications every day. Simply determine which applications you need from the catalog.
You can also add your corporate applications to the catalog within minutes using the SAML and OAuth protocols.
The Primary Actor of Security Risk: Passwords
The Role of Passwords in Our Lives
Passwords have been the primary actors in providing security in various fields from the past until the present. However, due to various attacks exposing the vulnerabilities of passwords and their susceptibility to easy guessing, they have led to a series of measures. Organizations first imposed complex password requirements and later increased the frequency of password changes to ensure the correct and secure access of customers and employees. These security enhancements have led to password-related issues, such as users forgetting their passwords, writing them down, and causing extra burdens on the Help Desk, ultimately increasing operational costs.
“61% of data breaches are due to weak or stolen passwords.”
Research has found that four out of five people reuse the same password across different accounts. This means that if one account is compromised, other accounts are at risk as well.
According to the Varonis 2019 Global Data Risk Report, 38% of users have passwords that never expire, indicating a 10% increase from the previous year. The same report revealed that 58% of companies observed inconsistent permissions for users.
Users, due to the difficulties of use, are now inclined to ease traditional identity verification methods and bend security policies. This has led to a 98% increase in Account Takeover (ATO) attacks.
Taking into account the solution costs related to passwords for Security Operations Teams (SOTs) and Help Desks established to prevent these attacks, the financial losses incurred by passwords in organizations have reached significant levels. In addition, the damage to reputation, which cannot be compensated for financially, has emerged as a significant loss.
Research has shown that APT groups mainly target governments and global companies.
Top 10 Targets of APT Groups in 2020
- Governments
- Banks
- Financial Institutions
- Politicians
- Telecommunication Companies
- Educational Institutions
- Defense Industry
- Energy Systems/Companies
- Law Enforcement
- Information Technology Companies
- Multi-Factor Authentication and OTP
The ever-increasing need for security has led to the addition of secondary, tertiary, and more factors to passwords, increasing security measures. However, over time, these additional security measures also began to present risks:
“Message interception of SMS/Email, determining future OTPs based on a certain number of obtained OTPs, and more.”
Two-factor authentication (2FA) and multi-factor authentication (MFA) became widely used in our lives, especially through financial institutions and public agencies. However, over time, all these security measures need to be applied alongside a password.
“A cyberattack occurs every 39 seconds.”
Data Breach Statistics
The financial losses resulting from data breaches secured by passwords are increasing at an alarming rate. In 2019, cybercrimes cost businesses more than 2 trillion dollars. In 2021, this figure reached 6 trillion dollars.
In the first six months of 2019, data breaches exposed 4.1 billion records (Forbes), and as of 2019, cyberattacks are considered one of the top five risks to global stability (World Economic Forum).
In 2019, First American Financial Corp. exposed 885 million records online, including bank transactions, social security numbers, and more (Gizmodo).
In 2019, financial and payment companies showed the largest drop in stock performance after a breach. Values decreased an average of 7.27% following a breach (Comparitech).
In 2019, the average employee had access to 17 million files and 1.21 million folders. (Varonis)
The average cost per record lost or stolen in a data breach is $150 (IBM).

This is end-to-end network security policy management for corporate firewalls. It’s a process that makes business operations more efficient, ranging from analysis to automation.
Today’s IT environments are more complex compared to the past, and there are some differences that make policy management more challenging.
Multiple Segments: Every new project or application introduces new network segments, which often result in the use of additional security firewalls.
Multi-Vendor Usage: Many companies commonly use at least two different vendors in their infrastructure.
Least Privilege Principle: Network access from two different IP addresses in different segments is provided on a need-to-know basis, with permissive rules being removed.
Cloud Usage: Hybrid cloud is frequently the preferred path to cloud adoption, often requiring the use of cloud security firewalls.
Situations like these lead to complex environments that require more rules to manage and more firewall demands to meet.
Network security policy management has become challenging in terms of policy change requests and policy tightening.
Opinnate is a system that makes network security policy management easy. Opinnate simplifies policy management by offering analysis, optimization, auditing, reporting, and automation features. It saves your time and effort while enhancing your organization’s security posture.
Opinnate provides a seamless approach to network security policy management, allowing you to focus on your core business objectives.
Provides a single console to view all firewall policies.
Automated policy tightening on firewalls reduces effort.
Enhances corporate security policy analysis and control mechanism for policy changes.
Enables zero-touch policy change automation.
Maintains compliance with regulations for the best industry practices for firewalls.
Detailed Features:
Opinnate NSPM provides a comprehensive range of features, including analysis, optimization, auditing, reporting, and automation, designed to enhance your organization’s overall security posture. By using our solution, you can save time and effort in managing your network security policies.
ZERO-TOUCH AUTOMATION:
Policy changes can be easily managed in real-life usage scenarios, no matter how complex or numerous the requests may be.
TO MANAGE ALLOWING RULES:
This mechanism is specific to Opinnate and is designed to collect only filtered syslog data for system performance and disk usage.
USER-BASED RULE CREATION:
Write your policies based on users rather than IP-based rules.
BEST PRACTICE-BASED RISK ASSESSMENT:
Always perform a risk assessment of your firewalls, identify shortcomings, and understand what measures you need to take.
END-DATE RULE MANAGEMENT:
Notify the owner before the rule expires to prevent any misunderstandings or interruptions.
MAKE YOUR APPLICATIONS MORE VISIBLE:
Group your policies for your applications so you can see the overall application map on the firewalls and streamline the policy change process.
EASILY COPY RULES FOR SERVERS:
Effortlessly clone policies for an existing server to a new server, even if it’s on a different IP subnet.
BE READY FOR ANY AUDIT:
Be prepared for any audit with predefined checklists and pass audits quickly.
Opinnate offers an innovative automation technology that brings a holistic approach to policy management. Designed by security experts with decades of execution and field experience, the Opinnate platform not only handles security policy management, policy analysis, policy optimization, and policy change processes under the same roof but also manages approval processes to provide an end-to-end customer experience. Opinnate stands out by eliminating dependencies on external tools and costly previous efforts.

Cast DDoS is automatically conducted by your DDoS test platform. In the basic usage of the web portal, you can easily select the attack type, the number of bots to be used, the attack duration, and schedule the attack. The platform simulates real DDoS attacks against organizations through actual attack parameters.
This allows organizations to test the limits and effectiveness of their DDoS prevention systems before facing a real DDoS attack. By using our platform, you can receive detailed reports, stop an attack in case of an emergency, get real-time assistance if needed, be informed before an attack, navigate during an attack, store your attack for later use, and stay informed about new attack types, all of which can be easily utilized.
Every infrastructure has its vulnerabilities:
DDoS testing subjects a web property or infrastructure to a realistic number of actual DDoS attacks to prove that your DDoS defenses can mitigate them as you expect.
DDoS testing is the only way to continuously test your website or infrastructure against an ever-evolving internet threat landscape. This is done by pushing the envelope of what you think your internet assets and properties need to be able to withstand with little to no impact on the performance of your network or website. Given that sophisticated attacks can render a website or an entire network infrastructure unusable, it is easier to test this than to assume that hackers won’t just throw traffic at a website and hope to cause issues, but rather they explore your system and setup to find vulnerabilities.
- Experience
At CastDDoS, we understand what a sophisticated attack entails and thoroughly test everything in our anti-DDoS environment. We stock our attack database with the latest attacks, including volumetric and some highly complex ones.
- Variety of Attacks
A wide variety of attacks in stock, each with multiple attack combination options; bandwidth, timing, and geographic location – dynamic selection of the number of bots.
- Stress Testing
The platform can be used to stress-test any portion of a website or network component.
- Do It Yourself
Access when you want, select or schedule an attack, stay informed before, during, and after; if you need an engineer to help you perform tests or a combination of both.
- Continuity Testing
Record previous tests and use the platform to test at any time, especially crucial after a website code change or network modification.
- Scale, Intensity, and Geographic Region
All attacks have parameters that allow you to throttle up or down at your own pace and store a specific custom test attack for later use.
- Victim Response
View how your IP or website responds to a specific attack in real-time. Some attacks may force you to respond with up to 20 times more bandwidth, leading to DDoS against your upstream provider.
- Performance Monitoring
Use our global performance monitoring service to view multiple metrics; some attacks can have a significant impact on your website’s performance. This is also used for legitimate stress testing.
- Emergency Stop
Emergency stopping capability in critical situations.
- Reporting
All attack test results can be viewed in real-time and are archived for download or viewing at any time through our customer portal.
- Sophisticated Attacks
Including VOIP attacks and VPN connection performance attacks.
To enhance your corporate network security and stay prepared against DDoS attacks, explore the services of Cast DDoS under the NETSYS guarantee.
Catch the Future with NETSYS.
Contact us to benefit from our network services.
