DNS Security
DNS security is a cornerstone of today’s internet and…
WAF Selection and Deployment Methods
We are pleased to share the recording of our…
Introducing Arista CloudVision Portal Studios!
On October 16th, we hosted an interactive webinar featuring…
The Potential of Blockchain Technology in Cyber Security
Blockchain technology has paved another way for innovative developments…
SIEM and SOAR Solutions
What is SIEM? SIEM (Security Information and Event Management),…
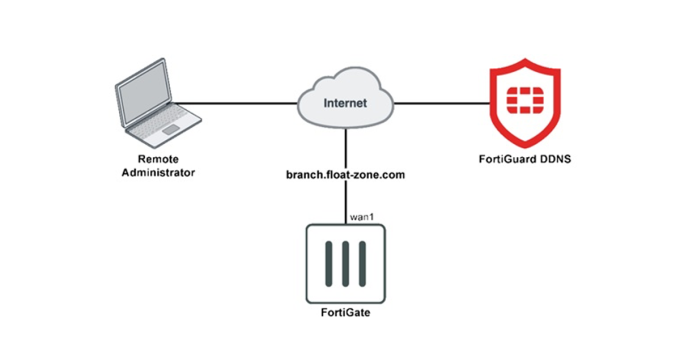
FortiGuard Dynamic DNS on Fortigate
In case the IP address of the internet line…
What is FortiDeceptor What It Does
In the event of an attack on the network,…
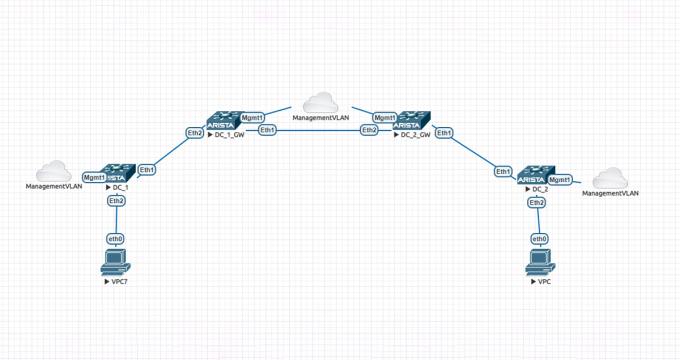
Automation Arista EVPN-VXLAN with Python
EVPN-VXLAN technology, which can be used to connect two…
Get to know our new partner, Cast DDoS.
What is CastDDoS? Cast DDos is done automatically by…
What are Half Proxy and Full Proxy?
What is Proxy? Proxy is a server application…
F5 Internet Access Permissions
In F5 BIG-IP and BIG-IQ systems, the necessary internet…
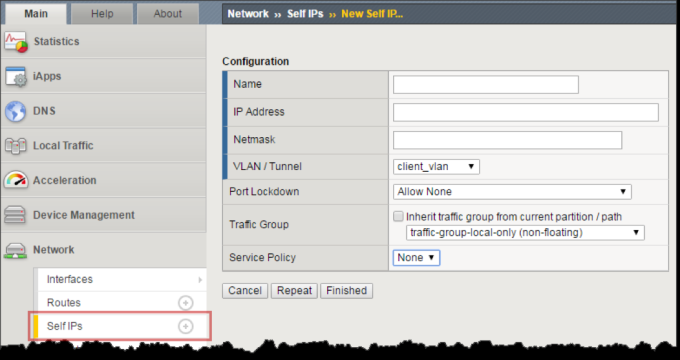
What is F5 Self IP and Floating Self IP Address?
Self IP Addresses (non-floating) Self IP addresses are configured…